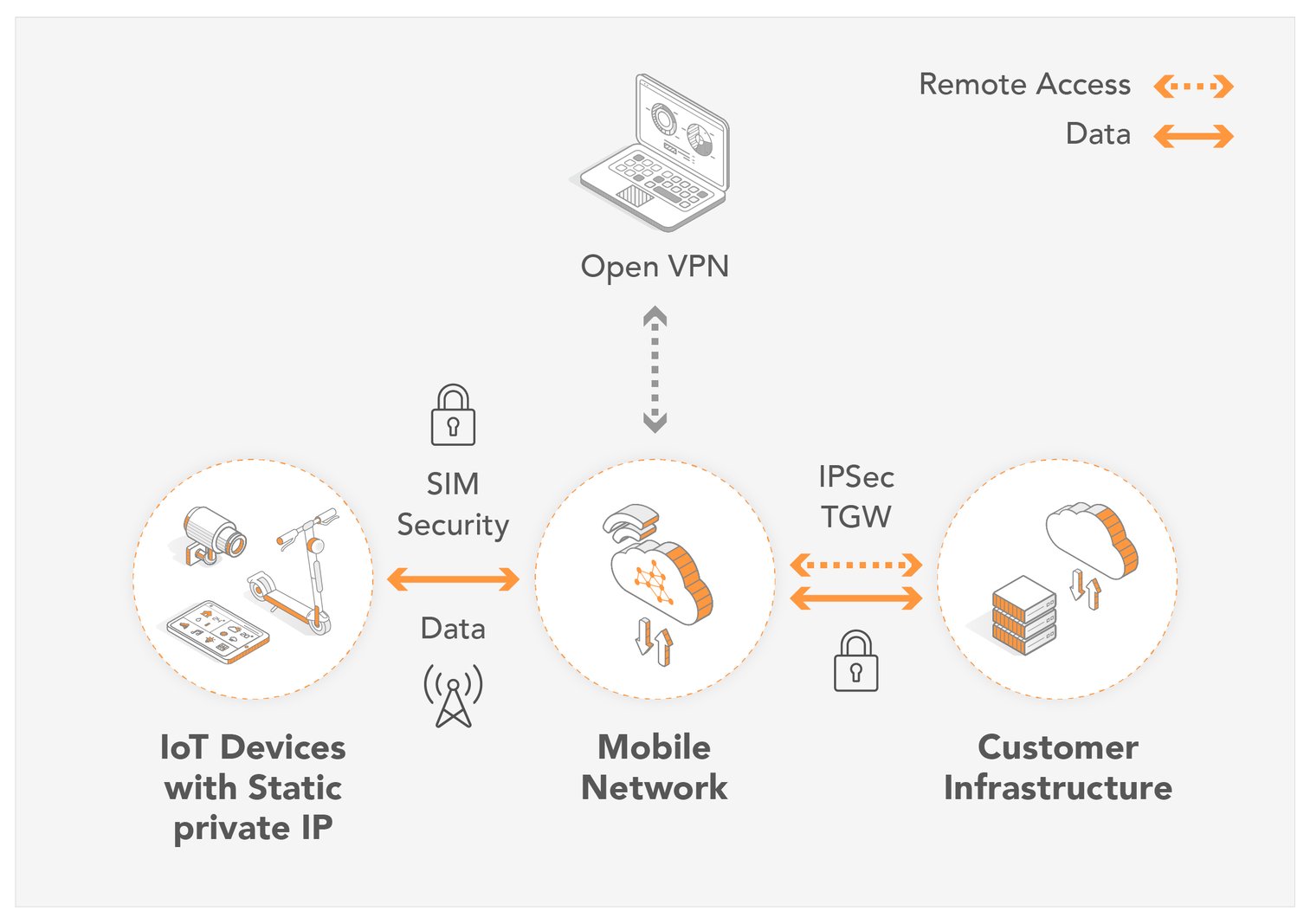
Are you truly confident that your IoT devices are secure from prying eyes and malicious actors? The reality is that without a robust security strategy, your IoT network is a ticking time bomb.
The Internet of Things (IoT) has revolutionized how we interact with technology, enabling seamless automation, unprecedented efficiency, and unparalleled convenience. However, this interconnectedness also introduces significant security vulnerabilities. Remote access, a cornerstone of IoT functionality, presents both opportunities and risks. One of the most prevalent methods for enabling this remote access is SSH, or Secure Shell. Understanding why SSH is crucial for IoT remote access, and how to secure it, is paramount for any individual or organization leveraging IoT technology.
| Information | |
|---|---|
| Full Name | N/A (This article does not focus on a specific individual) |
| Career/Profession | IoT Security Professional, Cybersecurity Expert, Network Administrator |
| Professional Information | Focuses on securing IoT devices and networks, implementing best practices for remote access, and mitigating vulnerabilities. Expertise in SSH, network segmentation, encryption, access control, and regulatory compliance. |
| Website | NIST Cybersecurity Framework (A valuable resource for cybersecurity best practices) |
IoT remote access refers to the ability to manage, monitor, and control IoT devices from a distant location. This capability is essential for a variety of applications, from smart home automation to industrial control systems. It allows businesses to troubleshoot issues, update software, and maintain devices without the need for physical presence, leading to improved operational efficiency and reduced costs. However, the convenience of remote access also opens up potential avenues for cyberattacks.
- Is It Over Michele Morrone Moara Sorios Relationship Timeline
- Movierulz Streaming What You Need To Know Guide
SSH provides a secure channel for remote access by encrypting the communication between the client and the server, preventing eavesdropping and unauthorized access. However, simply enabling SSH is not enough. Poorly configured SSH can become a major security risk, allowing attackers to gain control of IoT devices and potentially compromise entire networks. Therefore, implementing SSH security best practices is essential to safeguard your IoT ecosystem.
Why SSH is Crucial for IoT Remote Access
SSH provides a secure and encrypted communication channel, ensuring that sensitive data transmitted during remote access sessions remains confidential and protected from eavesdropping. Without SSH, data is transmitted in plain text, making it vulnerable to interception and manipulation. This is particularly critical in IoT environments, where devices often handle sensitive information, such as personal data, financial information, or industrial control parameters.
- Chlo Matt Tiktok Viral Pranks House Tours More
- Unlock Prison Break The Ultimate Guide To Seasons Streaming
SSH also provides strong authentication mechanisms, ensuring that only authorized users can access IoT devices remotely. SSH supports various authentication methods, including password-based authentication, public key authentication, and multi-factor authentication (MFA). Public key authentication is generally considered the most secure method, as it eliminates the need to transmit passwords over the network. MFA adds an extra layer of security by requiring users to provide multiple forms of identification, such as a password and a one-time code from a mobile app.
Furthermore, SSH enables secure file transfer, allowing users to securely upload and download files to and from IoT devices. This is essential for tasks such as updating software, configuring devices, and collecting data logs. SSH utilizes the Secure Copy Protocol (SCP) or the Secure FTP Protocol (SFTP) for secure file transfer, ensuring that files are protected from unauthorized access and modification.
Top 5 SSH Remote Access Solutions for IoT
Choosing the right SSH solution is crucial for securing your IoT environment. Here are five top SSH remote access solutions that offer robust security features and ease of use:
- OpenSSH: OpenSSH is a free and open-source implementation of the SSH protocol. It is widely used and highly regarded for its security and reliability. OpenSSH is available for a variety of operating systems, including Linux, macOS, and Windows. It supports various authentication methods, including password-based authentication, public key authentication, and GSSAPI authentication.
- Tectia SSH: Tectia SSH is a commercial SSH solution that offers advanced security features, such as strong encryption, multi-factor authentication, and intrusion detection. Tectia SSH is designed for enterprise environments and is compliant with various security standards, such as FIPS 140-2.
- Bitvise SSH Client: Bitvise SSH Client is a free SSH client for Windows that offers a user-friendly interface and a variety of features, including secure file transfer, terminal emulation, and port forwarding. Bitvise SSH Client is suitable for both personal and commercial use.
- PuTTY: PuTTY is a free and open-source SSH client that is available for a variety of operating systems, including Windows, Linux, and macOS. PuTTY is a lightweight and versatile SSH client that is widely used by developers and system administrators.
- AnyViewer: Whether you're a tech enthusiast managing remote devices or an IT professional overseeing the restoration of a client's equipment, AnyViewer simplifies the entire process.
How to Secure SSH Access for IoT Devices
Securing SSH access for IoT devices requires a multi-faceted approach that includes implementing strong authentication, configuring SSH securely, and monitoring SSH activity.
Strong Authentication:
- Disable Password-Based Authentication: Password-based authentication is vulnerable to brute-force attacks and should be disabled in favor of public key authentication.
- Enable Public Key Authentication: Public key authentication provides a more secure alternative to password-based authentication. It involves generating a pair of keys, a public key and a private key. The public key is stored on the IoT device, while the private key is kept secret by the user. When a user attempts to connect to the IoT device, the device uses the public key to verify the user's identity.
- Implement Multi-Factor Authentication (MFA): MFA adds an extra layer of security by requiring users to provide multiple forms of identification. This can include a password, a one-time code from a mobile app, or a biometric scan.
Secure SSH Configuration:
- Change the Default SSH Port: The default SSH port is 22. Changing the default port can help to prevent automated attacks that target the default port.
- Disable Root Login: Disabling root login prevents attackers from directly logging in as the root user. Instead, users should log in with a regular user account and then use the
sudocommand to execute privileged commands. - Use a Strong Cipher Suite: SSH supports various cipher suites, which are algorithms used to encrypt and decrypt data. Using a strong cipher suite ensures that data is protected from eavesdropping.
- Limit the Number of Authentication Attempts: Limiting the number of authentication attempts can help to prevent brute-force attacks.
- Set a Timeout for Inactive Sessions: Setting a timeout for inactive sessions can help to prevent unauthorized access if a user forgets to log out.
- Keep SSH Software Up to Date: Regularly updating SSH software ensures that you have the latest security patches and bug fixes.
Monitoring SSH Activity:
- Monitor SSH Logs: Regularly monitoring SSH logs can help to detect suspicious activity, such as failed login attempts, unauthorized access, or unusual network traffic.
- Use an Intrusion Detection System (IDS): An IDS can help to detect and prevent intrusions by monitoring network traffic and system logs for suspicious activity.
Security Considerations when Using SSH for Remote Access to Your IoT Device:
Enabling SSH on an IoT device introduces several security considerations that must be addressed to mitigate potential risks:
- Exposure to the Internet: Exposing an IoT device directly to the internet can significantly increase its attack surface. If possible, place IoT devices behind a firewall and use a VPN to establish a secure connection for remote access.
- Weak Passwords: Using weak or default passwords is a common security vulnerability that can be easily exploited by attackers. Always use strong, unique passwords and encourage users to change their passwords regularly.
- Unpatched Vulnerabilities: IoT devices often have unpatched vulnerabilities that can be exploited by attackers. Regularly update the firmware and software on your IoT devices to address known vulnerabilities.
- Malware Infections: IoT devices can be infected with malware, which can be used to steal data, launch attacks on other devices, or disrupt operations. Implement endpoint security solutions to protect your IoT devices from malware infections.
- Data Breaches: A successful attack on an IoT device can lead to a data breach, which can have serious consequences for individuals and organizations. Implement data encryption and access control measures to protect sensitive data stored on IoT devices.
Best Practices for IoT Remote Access
Adopting best practices for IoT remote access is crucial for ensuring a secure and efficient setup:
- Regular Security Audits: Conduct regular security audits to identify vulnerabilities and assess the effectiveness of your security measures.
- Network Segmentation: Segment your network to isolate IoT devices from other critical systems. This can help to prevent attackers from gaining access to sensitive data if an IoT device is compromised.
- Principle of Least Privilege: Grant users only the minimum level of access necessary to perform their tasks. This can help to prevent unauthorized access and data breaches.
- Regular Software Updates: Keep software and firmware up to date to patch security vulnerabilities.
- Monitoring Network Activity: Monitor network activity for suspicious patterns or anomalies.
- User Education: Educate users about security risks and best practices.
- Incident Response Plan: Develop an incident response plan to address security breaches.
The Growing Threat Landscape
Security issues are growing along with the number of IoT devices connected. As the number of IoT devices continues to increase exponentially, the attack surface for cybercriminals expands as well. IoT devices are often deployed in vulnerable environments, such as homes, offices, and industrial facilities, making them easy targets for attackers. This guarantees that even when viewed remotely controlled IoT, data and network infrastructure are secure.
Furthermore, many IoT devices are resource-constrained, meaning they have limited processing power, memory, and storage. This makes it difficult to implement robust security measures on these devices. As a result, many IoT devices are shipped with default passwords, unpatched vulnerabilities, and insecure configurations.
The consequences of a successful attack on an IoT device can be severe. Attackers can use compromised IoT devices to steal data, launch denial-of-service attacks, or even control physical infrastructure. In some cases, attackers have used compromised IoT devices to gain access to other systems on the network, leading to widespread data breaches.
Components of the Secure Remote Access Ecosystem
Secure remote access touches just about every aspect of enterprise security. A comprehensive secure remote access ecosystem includes various components, such as:
- Firewalls: Firewalls act as a barrier between your network and the outside world, preventing unauthorized access.
- Intrusion Detection Systems (IDS): IDS monitor network traffic and system logs for suspicious activity.
- VPNs: VPNs create a secure tunnel for remote access, encrypting all data transmitted between the client and the server.
- Multi-Factor Authentication (MFA): MFA adds an extra layer of security by requiring users to provide multiple forms of identification.
- Endpoint Security Solutions: Endpoint security solutions protect IoT devices from malware infections and other threats.
- Security Information and Event Management (SIEM): SIEM systems collect and analyze security logs from various sources, providing a centralized view of security events.
User Education and Cybersecurity Policies
Ensuring secure remote access requires more than just technological solutionsit also relies on user education, cybersecurity policies, and security hygiene best practices, which can reduce the chance of misconfigurations and accidental exposure. Users should be trained on how to identify phishing emails, how to create strong passwords, and how to protect their devices from malware. Cybersecurity policies should define acceptable use of IoT devices, remote access procedures, and incident response protocols.
Industrial Secure Remote Access Solutions
Industrial IoT (IIoT) environments present unique security challenges due to the critical nature of the infrastructure and the potential for physical harm. Industrial secure remote access solutions, such as those offered by Sectrio, are designed to address these specific challenges. These solutions typically include features such as:
- Network Segmentation: Isolating critical systems from other parts of the network.
- Access Control: Limiting access to sensitive data and systems.
- Anomaly Detection: Identifying unusual network traffic or system behavior.
- Threat Intelligence: Providing up-to-date information about emerging threats.
- Regulatory Compliance: Ensuring compliance with industry-specific regulations.
Evaluating Secure Remote Access Solutions
When evaluating secure remote access solutions, it is important to consider criteria such as robust encryption, MFA, and comprehensive access controls. Additionally, the reputation and support provided by the vendor are crucial factors in selecting the safest options. Consider the following factors:
- Encryption Strength: Ensure that the solution uses strong encryption algorithms to protect data in transit and at rest.
- Authentication Methods: Look for solutions that support multiple authentication methods, including MFA, to provide a layered security approach.
- Access Control: Verify that the solution offers granular access control features, allowing you to restrict access to specific resources based on user roles and permissions.
- Auditing and Logging: Choose a solution that provides comprehensive auditing and logging capabilities, allowing you to track user activity and identify potential security incidents.
- Vendor Reputation: Select a vendor with a proven track record of providing secure and reliable remote access solutions.
- Support and Maintenance: Ensure that the vendor offers adequate support and maintenance services to address any issues that may arise.
Mobile Device Management (MDM)
Mobile device management (MDM) solutions help manage the security of remote devices. MDM solutions offer flexibility and control over remote devices, regardless of location. These solutions provide features such as:
- Device Enrollment: Enrolling devices into the MDM system.
- Configuration Management: Configuring device settings and policies.
- Application Management: Deploying and managing applications on devices.
- Security Management: Enforcing security policies and detecting security threats.
- Remote Wipe: Remotely wiping data from lost or stolen devices.
OT Security Considerations
Managing security and risk in OT environments isnt as simple as porting over IT security best practices into the OT system. OT technology obsolescence periods are much longer. OT environments often use proprietary protocols and legacy systems that are not compatible with traditional IT security tools. Furthermore, OT environments require a different risk assessment approach that considers the potential for physical harm and disruption of critical infrastructure.
Security Experts' Solutions
Security experts have identified solutions to some common concerns raised by IoT. To guide your security practices, look at industry best practices and at lessons learned from law enforcement actions. Here are a few suggestions:
- Implement a Security Framework: Adopt a recognized security framework, such as the NIST Cybersecurity Framework, to guide your security practices.
- Conduct Regular Risk Assessments: Conduct regular risk assessments to identify vulnerabilities and assess the potential impact of security breaches.
- Implement Security Controls: Implement security controls to mitigate identified risks.
- Monitor Security Posture: Continuously monitor your security posture to detect and respond to security incidents.
- Stay Informed: Stay informed about emerging threats and vulnerabilities.
10 Best Practices for Secure Remote Work Access
Adopting these best practices can enhance remote access security in your organization:
- Implement MFA for all remote access points.
- Use strong and unique passwords.
- Keep software and firmware up to date.
- Use a VPN for remote access.
- Segment your network.
- Monitor network activity.
- Educate users about security risks.
- Implement an incident response plan.
- Conduct regular security audits.
- Enforce a strong password policy.
By implementing these strategies and best practices, organizations can significantly enhance the security of their IoT deployments and mitigate the risks associated with remote access. Embracing a proactive security posture is essential for harnessing the full potential of IoT while safeguarding against cyber threats.
- Easy Hey There Delilah Guitar Tutorial Chords Tabs
- Skymovieshd Is It Safe Reviews Downloads Alternatives