Are you truly confident that your smart refrigerator isn't a backdoor into your entire network? The proliferation of IoT devices has created a digital Wild West, and if you aren't securing these endpoints, you're leaving yourself dangerously exposed.
As Internet of Things (IoT) devices become ubiquitous in both consumer and industrial landscapes, they've naturally attracted the attention of malicious actors. A single IoT device can serve as a vulnerable entry point into an otherwise secure network. Indeed, attacks targeting IoT devices are on the rise, highlighting the urgent need for robust security measures. While adopting IoT devices can certainly boost productivity and provide valuable insights, it's crucial to address the inherent security risks.
| Topic | Description |
|---|---|
| IoT Device Security | Protecting Internet of Things devices and networks from unauthorized access, use, disclosure, disruption, modification, or destruction. |
| Remote Access Methods | Techniques used to access and control IoT devices from a remote location, including SSH, VNC, and RDP. |
| Secure Shell (SSH) | A cryptographic network protocol for operating network services securely over an unsecured network. Used for secure remote access. |
| Virtual Network Connection (VNC) | A graphical desktop-sharing system that allows you to remotely control another computer's screen. |
| Remote Desktop Protocol (RDP) | A proprietary protocol developed by Microsoft which provides a user with a graphical interface to connect to another computer over a network connection. |
| IoT Device Management | The process of monitoring, configuring, updating, and troubleshooting connected devices from a centralized platform. |
| Security Best Practices | Recommended measures and strategies to enhance the security of IoT devices and remote access connections, such as strong passwords, multi-factor authentication, and encryption. |
| Potential Threats | Risks and vulnerabilities associated with IoT devices, including malware infections, data breaches, and unauthorized control. |
| Cost of Downtime | The financial and operational impact of IoT device downtime, emphasizing the need for reliable and secure remote access solutions. |
| Access Control | Limiting user access to only the resources and data necessary to perform their tasks, minimizing the risk of accidental or intentional misuse. |
| Physical Security | Protecting IoT devices from physical threats through measures such as locks, passcodes, and security systems. |
| Edge Management | Managing and securing IoT devices at the edge of the network, closer to the data source. |
| Remote Monitoring | Using remote solutions to observe and manage IoT devices and their performance. |
| Unique Identifier | Assigning a unique identifier to each IoT device to ensure secure connection and data transfer over a protected network. |
This article will delve into the essential security considerations and best practices for secure shell (SSH) remote access to IoT devices. We'll provide tips to help you protect your IoT infrastructure from unauthorized access, ensuring its safety and integrity. Let's explore how to fortify your IoT devices against potential security threats.
- Jiohotstar Your Guide To Movies Series More Watch Now
- Aaron Pierres Wife Leah Dating Life Relationship Rumors
With the continuous growth in the number of IoT devices, identifying the most effective tools and methods for remote access is paramount. It's crucial to ensure efficiency, security, and ease of use when managing these devices remotely. This article serves as a guide, providing comprehensive insights into remote access to IoT devices using SSH. We'll cover essential tools, setup processes, and security practices.
One critical aspect to consider is the potential cost of IoT device downtime. Companies require reliable and secure remote access and support solutions to guarantee the uptime and usability of all their IoT devices. The financial stakes are simply too high to leave these devices vulnerable. Consider the retail industry, for instance, where downtime can lead to significant losses in sales and customer satisfaction.
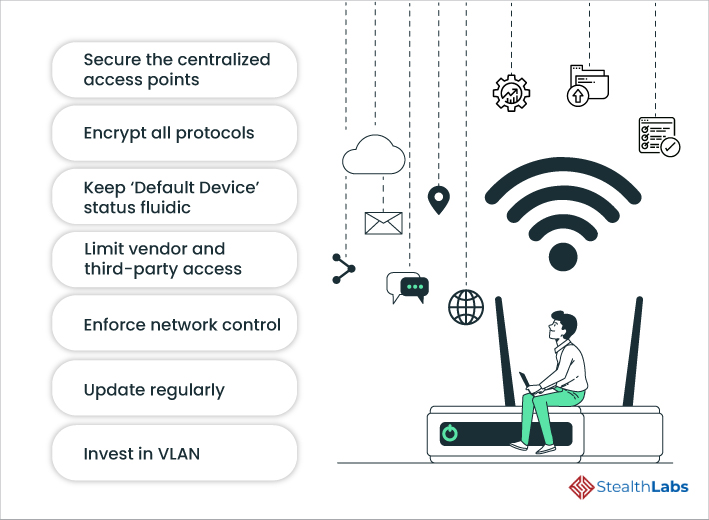
Securing your IoT SSH connections is paramount to safeguarding your devices and network. Here are some of the recommended best practices to consider and implement.
- Peter Dinklage Wife Erica Schmidt Kids Family Life Secrets
- Who Are David Bromstads Siblings Meet Dean Dynelle Dyonne
This discussion emphasizes the importance of secure remote access for IoT, exploring readily available free tools and methods. We will also provide actionable advice to protect your connected devices. Whether you're a homeowner managing smart home devices, a small business owner overseeing connected equipment, or an IT professional responsible for a complex IoT ecosystem, this guide equips you with the necessary knowledge to protect your assets effectively.
Access levels should be meticulously managed based on roles and responsibilities. A technician might require access solely for system maintenance, while a supervisor might need more extensive remote control capabilities. This approach minimizes the risk of inadvertent or intentional exploitation by ensuring that users only possess the privileges necessary to perform their assigned tasks.
If you're responsible for the IT infrastructure of a business, carefully consider who is granted access to specific computers containing sensitive information. Implement stringent access controls and regularly review user permissions to prevent unauthorized access and potential data breaches.
Digital security extends beyond the devices themselves. You must also prioritize the physical security of these devices, employing measures such as locks, passcodes, and robust business security systems. Preventing physical access can mitigate the risk of tampering and unauthorized modification.
Modern remote access solutions offer features that extend far beyond traditional screen sharing. These include terminal access, app control, and edge management, providing a comprehensive approach to addressing the complexities of IoT management. This is the future of efficient and secure IoT infrastructure.
In the context of the Internet of Things, remote access refers to the ability to connect to and control an IoT device from a remote computer or device. Several techniques can be employed for this purpose, including Secure Shell (SSH), Virtual Network Connection (VNC), and Remote Desktop Protocol (RDP). Each method offers unique advantages and considerations for security and performance.
Effective remote access streamlines the management of IoT devices at scale, resulting in improved operational efficiency and reduced risks. Centralized platforms enable administrators to monitor, configure, update, and troubleshoot connected devices from a single interface, simplifying maintenance and enhancing security oversight.
Remote IoT device management encompasses the ability to monitor, configure, update, and troubleshoot connected devices through a centralized platform. This includes tasks such as deploying software updates, configuring device settings, and diagnosing issues remotely. Centralized management provides greater visibility and control over the entire IoT ecosystem.
To establish healthy remote work security, a strong focus on IoT is essential. These connected Internet of Things devices must be secured to prevent unauthorized access and data breaches. Implementing security measures tailored to IoT devices is crucial for maintaining a secure remote work environment.
Each device must be granted a unique identifier, enabling it to connect and transfer data securely over a protected corporate network. This helps in tracking and managing devices, as well as preventing unauthorized devices from accessing the network.
When adding an access method, ensure that you fill in or choose the information appropriate to each access method listed. Refer to specific method for detailed instructions and configuration settings. Accurate configuration is crucial for ensuring secure and reliable remote access.
Remote SSH access empowers you to maintain control, reduce downtime, and improve your IoT device management by eliminating the need for physical proximity to your device. This allows for greater flexibility and responsiveness in managing IoT devices, regardless of their location.
Secure remote access impacts nearly every aspect of enterprise security. It's essential to consider all potential vulnerabilities and implement security measures accordingly. A holistic approach to security ensures that all components of the remote access ecosystem are protected.
Ensuring secure remote access to SSH IoT devices behind firewalls and NAT routers is of utmost importance in the rapidly evolving world of managing Internet of Things devices. Proper configuration and security measures are essential for protecting these devices from unauthorized access and cyber threats.
This discussion explores remote IoT device management, focusing on secure methods to access Raspberry Pi web devices remotely. We will delve into two key methods, providing practical guidance on implementing secure remote access for these popular IoT devices.
Begin by navigating to the device's settings and enabling remote access. Follow the pairing instructions provided in the app to connect your device to your account. Accurate configuration is crucial for establishing a secure and reliable remote connection.
Adjust user permissions and access levels to control who can remotely access the device. Limiting access to authorized personnel only is essential for preventing unauthorized access and potential security breaches.
IoT (Internet of Things) remote monitoring solutions have revolutionized the way businesses manage their operations. Remote monitoring enables businesses to track and manage their IoT devices in real-time, providing valuable insights and improving operational efficiency.
In the intricate dance of digital connection, remote IoT access methods and security tips are your essential choreography. You need to know them. The choreography to keep you safe!
- Kannada Movies 2025 Trailers Reviews Where To Watch
- Jeff Ross Health Update Truth Behind The Rumors Find Out Now