Are you truly confident in the security of your IoT devices? Organizations must adopt robust Remote IoT SSH key management strategies to fortify defenses against ever-evolving cyber threats.
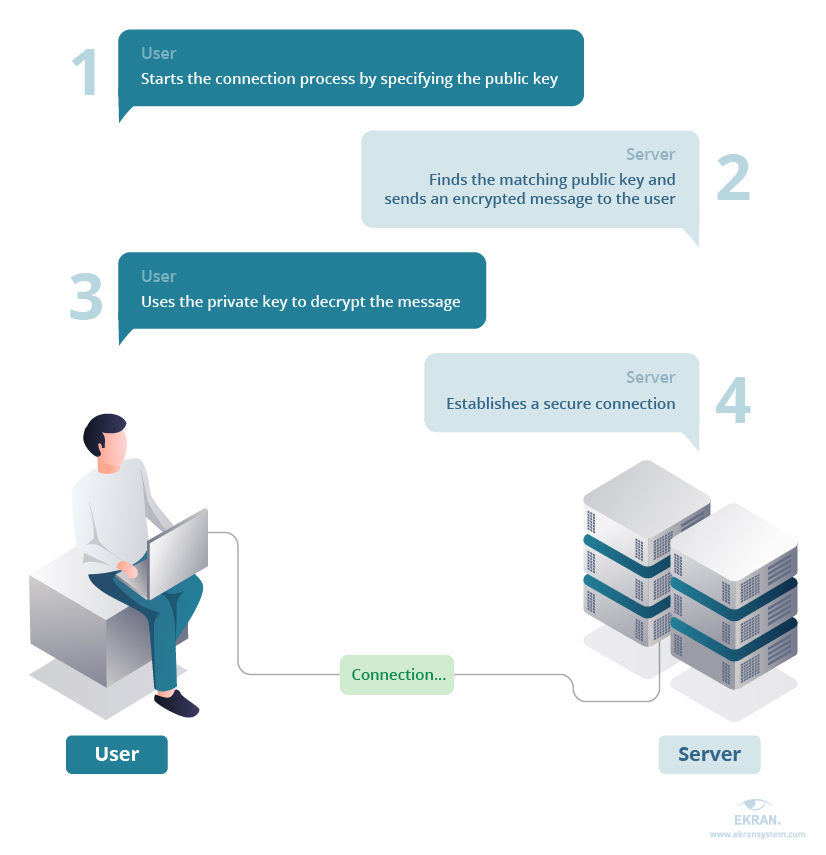
In an era where the Internet of Things (IoT) is rapidly expanding, connecting everything from smart thermostats to critical industrial control systems, the security of these devices has never been more paramount. Secure Shell (SSH) tunneling plays a vital role, acting as a secure conduit for communication between users and remote servers, networks, and devices. This is achieved through established firewalls and gateway routers, utilizing assigned and protected ports. SSH facilitates the secure transfer of internet traffic between local and remote devices, forming the backbone of many remote management and data transfer operations.
| Category | Information |
|---|---|
| Name | N/A (General Topic) |
| Profession | Cybersecurity Professional, Network Administrator, IT Enthusiast |
| Focus | Remote IoT SSH Key Management |
| Organization | Any organization utilizing remote IoT devices |
| Website | OWASP (Open Web Application Security Project) |
However, the increasing reliance on SSH also introduces significant security implications. Enabling SSH on an IoT device, like any remote access solution, opens potential vulnerabilities that malicious actors can exploit. Therefore, understanding and implementing best practices for SSH key management is not just advisable; it's an absolute necessity.
- Brad Dourif Beyond Chuckys Voice A Career Retrospective
- Chloandmatt Tiktok Pranks Hilarious Couple Moments House Tour
SSH key management is the cornerstone of securing remote IoT devices. These keys, when properly managed, provide a robust authentication mechanism, far superior to traditional password-based systems. But without careful oversight, SSH keys can quickly become liabilities. A compromised or poorly managed key can grant attackers unrestricted access to sensitive systems, allowing them to steal data, disrupt operations, or even gain control of the device itself. SSH tunneling provides the channel; proper key management is the lock on the door.
Recent findings underscore the urgency of this issue. A report by SSH Communications Security revealed a concerning trend: over 80% of enterprises possess SSH keys that are more than three years old. This alarming statistic significantly increases the risk of unauthorized access, as older keys are more susceptible to compromise through brute-force attacks, key theft, or insider threats. The longer a key remains in use, the greater the likelihood that it will be exposed to potential vulnerabilities.
Effectively managing SSH keys for remote IoT devices demands a strategic and multifaceted approach. It's not enough to simply generate keys; organizations must implement comprehensive policies and procedures to govern the entire SSH key lifecycle, from creation and distribution to storage, rotation, and revocation. This lifecycle management is essential for maintaining the integrity and security of remote access to IoT devices.
Adopting best practices for Remote IoT SSH can drastically improve the security and operational efficiency of your IoT infrastructure. These practices are designed to minimize risk, streamline access control, and ensure that only authorized users and devices can connect to your sensitive systems. Lets consider essential security considerations when utilizing SSH for remote access to IoT devices:
- Update your SSH keys periodically to minimize the risk of compromise. Key rotation is a fundamental security practice. Regularly changing SSH keys limits the window of opportunity for attackers to exploit compromised keys. The frequency of rotation should be determined based on the sensitivity of the data and systems being protected.
- Restrict which users and devices can use specific keys. Implement granular access controls to limit the scope of each key's permissions. This principle of least privilege ensures that even if a key is compromised, the attacker's access is limited to only the resources that key was authorized to access.
- Use SSH keys for authentication instead of passwords for enhanced security. Passwords, especially weak or reused passwords, are a common entry point for attackers. SSH keys provide a much stronger authentication mechanism, as they are based on cryptographic principles and are far more resistant to brute-force attacks.
- Restrict SSH access to authorized users and IP addresses. Implement network-level access controls to limit SSH connections to only trusted sources. This can be achieved through firewalls, access control lists (ACLs), and other network security devices.
- Change Default SSH Port. One of the most basic, yet often overlooked security measures, is to change the default SSH port (22). Attackers commonly target this port for brute-force attacks. Changing the port to a non-standard value can significantly reduce the number of automated attacks your server receives.
The process of effectively managing SSH keys presents numerous challenges. With the vast numbers of SSH keys possessed by organizations, manual processes are simply infeasible. The sheer scale of key management, coupled with the complexity of IoT environments, demands automation. Managing SSH keys manually is prone to errors, inconsistencies, and delays, increasing the risk of security breaches.
SSH key management platforms, sometimes referred to as SSH key management systems or solutions, address these challenges by providing a centralized and automated approach to managing SSH. These platforms automate key generation, distribution, storage, rotation, and revocation, streamlining the entire SSH key lifecycle. This automation not only reduces the risk of human error but also significantly improves security, efficiency, and availability.
All processes related to the management of SSH keys can be optimized by automating the SSH key lifecycle. Automation ensures consistency, enforces security policies, and reduces the administrative burden on IT staff. By automating key management, organizations can free up resources to focus on other critical security tasks. Most importantly, automation can significantly improve security, efficiency, and availability.
Implementing security best practices is essential for protecting your SSH server from unauthorized access and potential attacks. This goes beyond simply using strong keys. Organizations must also implement robust monitoring and logging capabilities to detect and respond to suspicious activity. Regular security audits and penetration testing can also help identify and address vulnerabilities in your SSH infrastructure.
The rise in cyberattacks targeting IoT devices necessitates a deep dive into understanding and implementing the best practices for SSH key management. Cybersecurity threats are increasingly targeting operational technology (OT) environments. These systems are essential for the functioning of critical infrastructure, including energy grids, manufacturing plants, and transportation networks. Protecting these systems from unauthorized access is paramount.
Managing SSH keys for remote IoT devices requires a strategic approach. It's a continuous process that requires ongoing monitoring, evaluation, and improvement. Organizations must stay abreast of the latest security threats and vulnerabilities and adapt their SSH key management practices accordingly.
This guide explores the best practices, tools, and strategies to effectively manage SSH keys for remote IoT devices, ensuring maximum security and operational efficiency. Whether you're a network administrator, cybersecurity professional, or IT enthusiast, this article will provide you with actionable insights into the world of SSH key management.
Transferring data between an IoT device and a local or remote server requires secure channels. SSH tunneling provides that secure channel, but it's the strength of the SSH keys that determines the overall security of the connection. Weak or compromised keys can undermine the entire security architecture.
Once these practices are implemented, protect your organization from future attacks and advanced cryptography by diving into the following best practices for secure remote access policies. Securely back up important data to a remote location, ensuring business continuity in the event of a security breach or disaster.
Solutions offered by SSH Communications Security, such as Privileged Access Management (PAM) and SSH key management systems, provide a range of options to suit different environments. Selecting an optimal solution is about finding the right balance between security, usability, and integration with existing technologies.
SSH PrivX OT Edition is designed to help organizations tackle the growing security challenges of IoT and OT environments. It provides a centralized and automated approach to managing SSH access, ensuring that only authorized users and devices can connect to critical systems.
Adopting best practices for Remote IoT SSH can significantly improve the security and efficiency of your IoT infrastructure. This section will outline key best practices to consider when implementing SSH for IoT devices. Keep your SSH software up to date to patch security vulnerabilities and ensure compatibility with the latest security standards.
Lost or compromised private keys can grant attackers unauthorized access to critical systems. Protecting these keys is paramount. Implement robust key storage mechanisms, such as hardware security modules (HSMs) or secure enclaves, to protect private keys from theft or unauthorized access.
- Shawn Mendes Finally Addressing Sexuality Rumors The Truth
- Bollyflix Download Guide Safe Legal Movie Streaming Alternatives