Are you truly in control of your digital world? You absolutely can be, and securing remote access to your Internet of Things (IoT) devices is the key to unlocking that power.
In an increasingly interconnected world, the ability to remotely access and manage IoT devices is no longer a luxury; it's a necessity. From smart homes brimming with interconnected appliances to industrial environments teeming with sensors and actuators, IoT devices have become integral to our lives and businesses. But with this increased connectivity comes increased risk. The potential for unauthorized access, data breaches, and malicious attacks looms large. That's where secure remote access solutions come into play, offering a lifeline for safeguarding connections, preserving data privacy, and streamlining device management. This exploration into the realm of remote IoT access delves into the critical aspects of securing these connections, offering a comprehensive guide to beginners and seasoned professionals alike.
| Category | Information |
|---|---|
| Concept | Remote IoT Access Security |
| Definition | Methods and technologies used to securely connect to and manage IoT devices from a remote location. |
| Key Technologies | SSH, VPNs, TLS/SSL, Firewalls, SIEM software |
| Benefits | Enhanced Security, Improved Efficiency, Streamlined Management, Real-time Monitoring |
| Risks of Poor Security | Data Breaches, Unauthorized Access, Device Hijacking, System Disruption |
| Beginner Setup Considerations | Device Compatibility, Firmware Updates, Router Configuration, Strong Passwords |
| Advanced Security Measures | Multi-Factor Authentication, Intrusion Detection Systems, Regular Security Audits |
| Reference Website | NIST Cybersecurity Framework |
The cornerstone of secure remote access for many IoT devices is Secure Shell (SSH). The best remote IoT device SSH solutions play a crucial role in safeguarding connections, preserving data privacy, and streamlining device management. This seemingly simple protocol provides an encrypted channel for communication, protecting sensitive data from prying eyes. SSH allows administrators to remotely configure devices, transfer files securely, and diagnose issues without physically being present. This functionality is invaluable in scenarios ranging from updating firmware on a remote sensor in an agricultural field to troubleshooting a malfunctioning smart thermostat in a vacation home. Understanding the nuances of SSH, including key generation, authentication methods, and security best practices, is paramount for anyone responsible for managing IoT devices.
- Movies4u Free Streaming Find It Here Guide
- Clea Duvall Career Relationships Detroit Rock City Then Now
This guide will explore the best SSH remote access tools for IoT, focusing on security, ease of use, and scalability. It will provide practical advice on selecting the right tools for specific use cases, configuring them properly, and maintaining a secure environment. The aim is to empower readers to take control of their IoT infrastructure and minimize the risk of cyber threats.
Setting up SSH on your IoT device is often a straightforward process, but it requires careful attention to detail. Many IoT devices, particularly those running Linux-based operating systems, come with SSH servers pre-installed. However, these servers are often configured with default settings that can leave them vulnerable to attack. It's crucial to change default passwords, disable unnecessary features, and implement strong authentication mechanisms. For devices that don't have a built-in SSH server, there are lightweight implementations available that can be easily installed and configured.
Before diving into the technical details of SSH configuration, it's essential to assess the compatibility of your IoT devices with remote access protocols. Check if your IoT devices are compatible with remote access protocols and verify if the devices have the required firmware or software that supports remote control. Not all devices are created equal, and some may lack the necessary hardware or software to support SSH or other remote access methods. Consult the device's documentation or contact the manufacturer to determine its capabilities. Furthermore, ensure that the device's firmware is up to date. Firmware updates often include security patches that address known vulnerabilities, and keeping devices up to date is a fundamental step in maintaining a secure environment.
- Sharon Logonov Chipper Jones Divorce Details More
- Shannon Sharpes Kids Love Life What You Need To Know
Beyond SSH, other security measures are essential for protecting remote IoT access. Enable a robust firewall and update router firmware for. A firewall acts as a barrier between your IoT devices and the outside world, blocking unauthorized access attempts. Modern routers typically include built-in firewalls that can be configured to restrict traffic based on source IP address, destination IP address, port number, and other criteria. Regularly updating your router's firmware is also crucial, as these updates often include security patches and performance improvements. Neglecting these basic security measures can leave your entire network vulnerable to attack.
The landscape of cybersecurity is constantly evolving, and new threats emerge on a daily basis. Find out how SIEM software helps organizations recognize and address potential security threats and vulnerabilities before they disrupt business operations. Security Information and Event Management (SIEM) software provides a centralized platform for collecting, analyzing, and reporting on security events from across your network. SIEM tools can help you identify suspicious activity, detect intrusions, and respond to incidents in a timely manner. While SIEM software can be complex to implement and manage, it's an invaluable tool for organizations with a large number of IoT devices or those that handle sensitive data.
The cloud has become an integral part of many IoT deployments, providing a platform for data storage, processing, and analysis. Secure your cloud environment with cloud security, a collection of procedures and technology, to address external and internal threats to business security. Protecting your cloud environment is just as important as securing your devices themselves. Cloud providers offer a range of security services, including firewalls, intrusion detection systems, and data encryption, but it's your responsibility to configure these services properly and monitor them for suspicious activity. Implementing strong access control policies and regularly auditing your cloud environment are essential steps in maintaining a secure cloud presence.
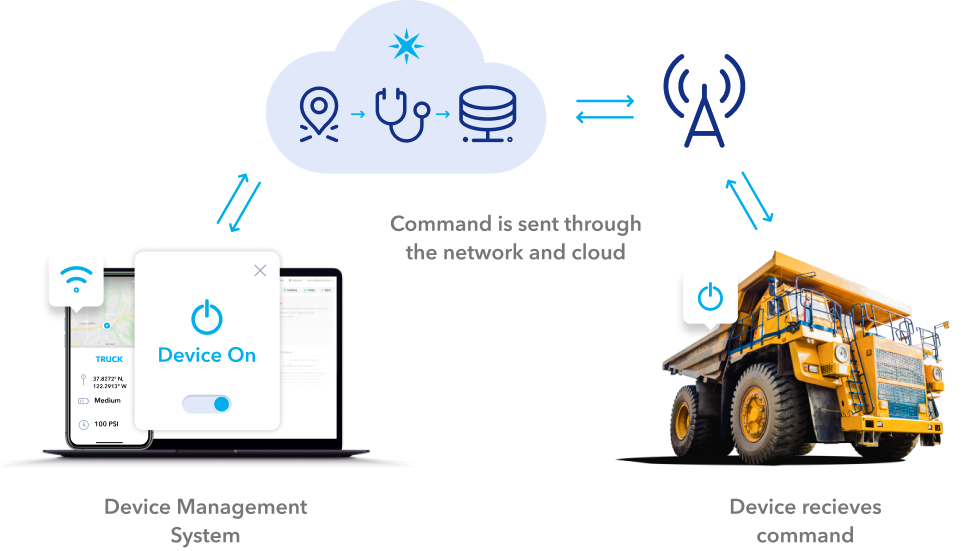
Remote access to IoT devices offers numerous advantages, but it also introduces new security challenges. Key benefits of remote access to IoT devices. Understanding these challenges and implementing appropriate security measures is essential for mitigating risk.
Remote access to IoT devices offers numerous advantages that enhance efficiency, productivity, and security: Enables continuous monitoring and immediate control of IoT devices, allowing for swift responses to any issues or adjustments needed. One of the primary benefits of remote access is the ability to monitor and control devices from anywhere in the world. This enables proactive maintenance, rapid response to emergencies, and improved operational efficiency. For example, a farmer can remotely monitor soil moisture levels and adjust irrigation systems as needed, optimizing water usage and maximizing crop yields. A building manager can remotely control HVAC systems to optimize energy consumption and ensure occupant comfort. The possibilities are endless.
Control lights, appliances, and security systems based on sensor data. The ability to automate tasks based on sensor data is another key benefit of remote IoT access. Smart homes can automatically adjust lighting and temperature based on occupancy and environmental conditions. Security systems can automatically arm or disarm based on time of day or location. Industrial processes can be optimized based on real-time sensor data, improving efficiency and reducing waste. Automation not only saves time and money but also improves safety and security.
Monitor soil moisture and weather conditions for precision farming. In the realm of agriculture, remote access to IoT devices is transforming the way crops are grown. Farmers can use sensors to monitor soil moisture, weather conditions, and plant health, and then use this data to optimize irrigation, fertilization, and pest control. This precision farming approach can lead to increased yields, reduced water consumption, and decreased reliance on pesticides and herbicides. Remote access also allows farmers to monitor their crops from anywhere in the world, enabling them to respond quickly to changing conditions and prevent losses.
Track vital signs like heart rate and oxygen levels remotely. In the healthcare industry, remote patient monitoring is becoming increasingly prevalent. Wearable devices can track vital signs such as heart rate, blood pressure, and oxygen levels, and transmit this data to healthcare providers in real-time. This allows doctors to monitor patients remotely, identify potential problems early on, and provide timely interventions. Remote patient monitoring can improve patient outcomes, reduce hospital readmissions, and lower healthcare costs.
After finishing the comprehensive guide on building a full network using #opnsense, i've decided to create a more simplified version for beginners that may b. The world of network security can seem daunting, especially for beginners. Understanding concepts like firewalls, VPNs, and intrusion detection systems can be overwhelming. That's why it's essential to start with a simplified approach and gradually build your knowledge and skills. Numerous online resources, tutorials, and courses are available to help you learn the fundamentals of network security. Don't be afraid to experiment and try new things, but always remember to back up your data and proceed with caution.
Stay informed about best security practices and vendor reputations to ensure a secure and reliable remote access setup. Choosing the right vendors for your IoT security needs is crucial. Look for vendors with a proven track record of security and reliability. Read reviews, consult industry analysts, and ask for references. Don't be afraid to ask vendors about their security practices and certifications. A reputable vendor should be transparent about their security measures and willing to answer your questions.
With remote access to your IoT devices, you can enjoy the convenience of controlling your devices from anywhere, improving efficiency, security, and peace of mind. Embracing remote IoT access is about empowering yourself with control, efficiency, and above all, security. By carefully selecting the right tools, implementing robust security measures, and staying informed about the latest threats, you can unlock the full potential of your IoT devices without compromising your privacy or security.
- Snl 50 Red Carpet Blake Lively Kim K More Pictures
- Is Megan Is Missing Good A Dark Twist Film Analysis More